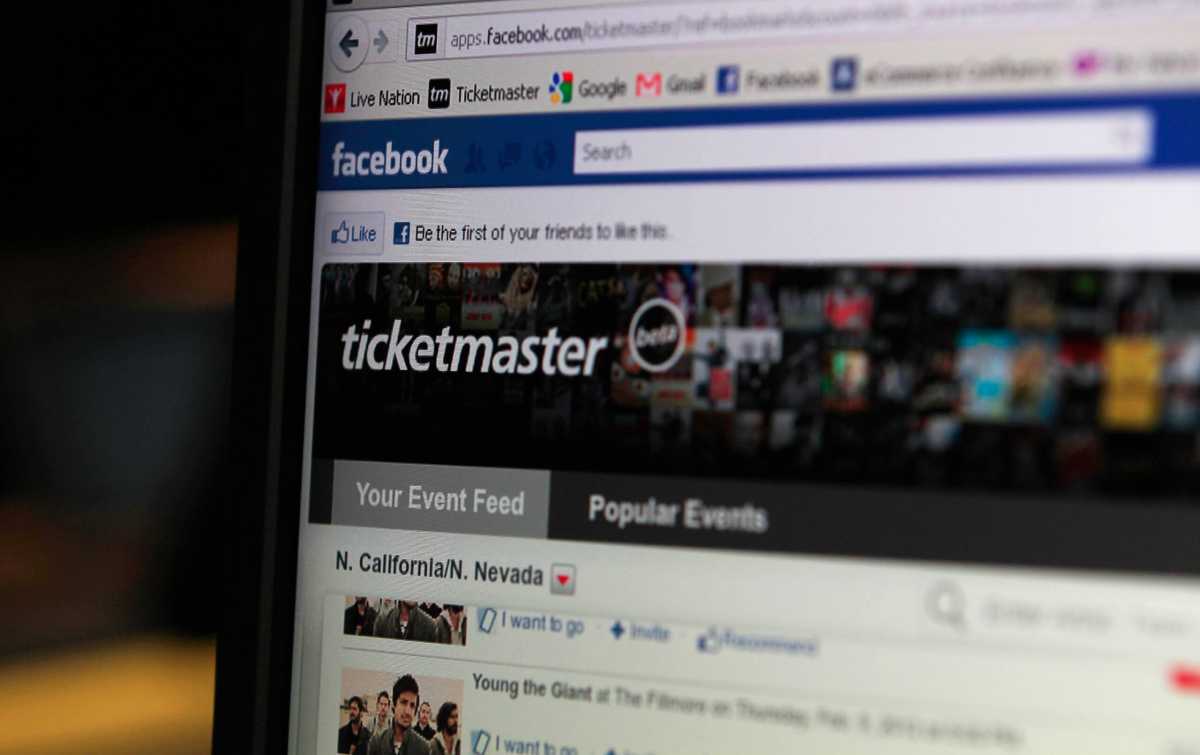
Ticketmaster agreed to pay a huge fine to resolve charges that it repeatedly accessed without authorization the computer systems of a competitor over the course of a few years.
The Eastern District of New York announced that Ticketmaster will pay the $10 million criminal fees in connection to the crimes. On Oct. 18, 2019, Ticketmaster’s former head of Artist Services Zeeshan Zaidi, 46, pled guilty in a related case to conspiring to commit computer intrusions and wire fraud based on his participation in the same scheme.
“Ticketmaster employees repeatedly – and illegally – accessed a competitor’s computers without authorization using stolen passwords to unlawfully collect business intelligence,” stated Acting U.S. Attorney Seth DuCharme. “Further, Ticketmaster’s employees brazenly held a division-wide ‘summit’ at which the stolen passwords were used to access the victim company’s computers, as if that were an appropriate business tactic. Today’s resolution demonstrates that any company that obtains a competitor’s confidential information for commercial advantage, without authority or permission, should expect to be held accountable in federal court.”
According to court filings and Ticketmaster’s own admissions, Ticketmaster was primarily engaged in the business of selling and distributing tickets to events and concerts as a wholly-owned subsidiary of Live Nation Entertainment, Inc. The victim company, which is based in the United Kingdom, offered artists the ability to sell presale tickets through an online ticketing platform, while also offering artists an Artist Toolbox (called the Toolbox), which was a password-protected app that provided real-time data about tickets sold through the victim company.
Ticketmaster’s coconspirator, whose identity has not been disclosed at this time, was a former senior employee of the victim company and worked in the company’s Brooklyn offices from May 2010 to July 2012. At the time of his departure, the coconspirator signed a separation agreement with the victim company, in which he agreed to maintain the confidentiality of that company’s confidential information. He then joined Live Nation in approximately August 2013.
While employed by Live Nation, the coconspirator shared the URLs for draft ticketing web pages that the victim company had built for an artist, but had not disseminated to the public, with Zaidi and another Ticketmaster employee in November 2013. In response to a Ticketmaster executive explaining that the goal was to “choke off [victim company]” and “steal back one of [victim company]’s signature clients,” the coconspirator offered that Ticketmaster could “cut [victim company] off at the knees” if they could win back presale ticketing business for a second major artist that was a client of the victim company.
In January 2014, the coconspirator emailed Zaidi and another Ticketmaster executive multiple usernames and the corresponding passwords for Toolboxes, with the coconspirator encouraging the executives to “screen-grab the hell out of the system.” The coconspirator also warned that “I must stress that as this is access to a live [victim company] tool I would be careful in what you click on as it would be best not [to] giveaway that we are snooping around.” The information from the Toolboxes was used to create a presentation for other senior executives that was intended to “benchmark” Ticketmaster’s offerings against those of the victim company.
In May 2014, a senior executive at Live Nation, whose identity was not disclosed, asked how Ticketmaster’s presale online offering compared with the Toolbox. When the coconspirator was then asked to “do a screenshare/demo” at an upcoming “Artist Services Summit,” they agreed to “pull together a list of the log-ins and URL’s that I still have access to for this so I can give the team as much insight as possible.” At least 14 Live Nation and Ticketmaster employees attended the summit in San Francisco and the coconspirator used a username and password he had retained from his employment at the victim company to log in to a Toolbox, and provided a demonstration. Coconspirator later provided Zaidi and other Ticketmaster executives with internal and confidential financial documents he had retained from his employment at the victim company.
The coconspirator was transferred to the Artist Services division, promoted to Director of Client Relations and given a raise in January 2015. Following the promotion, the coconspirator emailed another Artist Services employee, “Now we can really start to bring down the hammer on [Victim Company].” Ticketmaster employees continued to access password-protected victim company Toolboxes through December 2015.
Court records say that between July 2014 and June 2015, the coconspirator and others within the company monitored draft ticketing web pages created by the victim company. Although these pages were not password-protected, they were not indexed in search engines, and therefore could not be located without determining the exact URLs, which included a series of numbers, so until the victim company or artist publicly disseminated a URL, the victim company intended to restrict access to itself and the artist.
The coconspirator explained to Zaidi and others after joining Live Nation how the store ID numbers in the URLs numbers in the URLs were numbered sequentially, enabling Ticketmaster employees to monitor new pages and to learn which artists planned to use the victim company to sell tickets. The coconspirator used this information to search for new ticketing webpages from the victim company and sent the URLs to Ticketmaster executives. In or about January 2015, a Ticketmaster employee was assigned to learn about this system from coconspirator and maintained a spreadsheet listing every victim company ticketing web page that could be located, so that Ticketmaster could identify the victim company’s clients and attempt to dissuade them from selling tickets through the victim company. Zaidi explained that “we’re not supposed to tip anyone off that we have this view into [the victim company’s] activities.”
As a result of these crimes, Ticketmaster will pay a criminal penalty of $10 million and will maintain a compliance and ethics program designed to prevent and detect violations of the Computer Fraud and Abuse Act and other applicable laws, and to prevent the unauthorized and unlawful acquisition of confidential information belonging to its competitors, under the terms of the deferred prosecution agreement. Ticketmaster will also report to the United States Attorney’s Office annually during the three-year term of the agreement regarding these compliance measures. Should Ticketmaster breach this agreement, it will be subject to prosecution for the charges of conspiracy to commit computer intrusions, computer intrusion for commercial advantage, computer intrusion in furtherance of fraud, wire fraud conspiracy and wire fraud.
“Ticketmaster terminated both Zaidi and [the coconspirator] in 2017, after their conduct came to light. Their actions violated our corporate policies and were inconsistent with our values. We are pleased that this matter is now resolved,” said a Ticketmaster spokesperson.
Updated at 4:51 p.m.